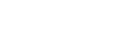Beholden smiles
Hearty handshakes
Grateful letters
Renewed contracts

The result precisely as promised
We carry out IT services accurately and in earnest

Meticulous IT costs calculations
We follow your technology needs and financial capacity

Reliable and responsive IT partners
We do everything to prevent business interruptions

We
are Parasol Software,
Dubai-based IT company
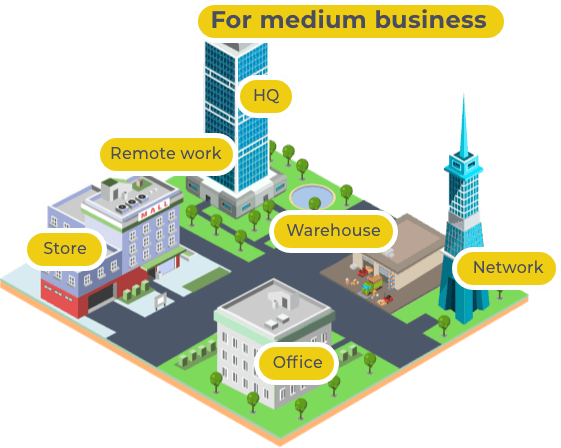
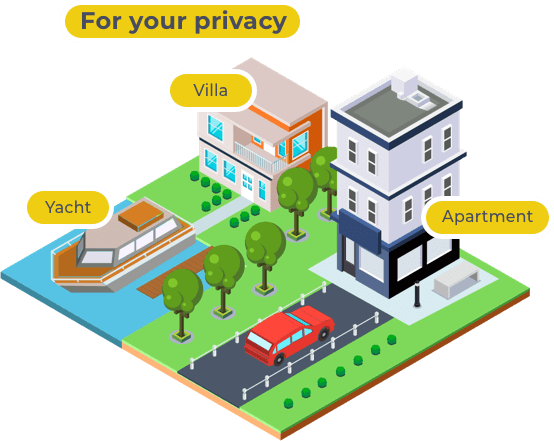
From the start line, Parasol Software aspires to the title of a driver of the UAE outsourcing IT service industry. Our crew members draw an inspiration from innovations but put a client’s business needs first. We cooperate with the best tech vendors and IT distributors in Dubai and attentively follow the latest initiatives and around the world to add them to our comprehensive portfolio. Our IT company offers a complex of customized solutions for individuals, small business entrepreneurs, medium business (100- 200 employees) managers and owners. Our strategy is to analyze the goals of a client, the budget and the venue capacity and fuel the business or the household with the most suitable technologies.


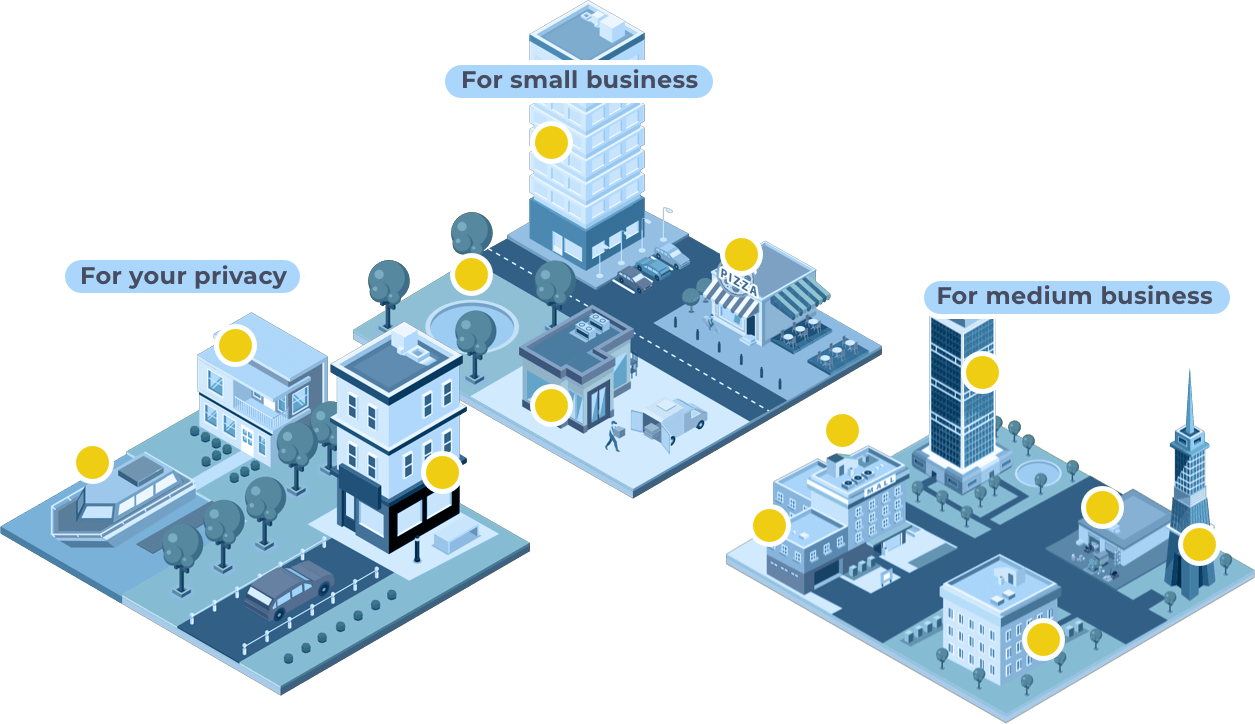
Move your mouse over a part of
the illustration to see details

We have the right IT solution
IT Support
- Reanimation of applications and software after abrupt crashes.
- Urgent data recovery.
- Network and WiFi connection issues elimination.
Outsourcing IT Support
- A workspace setup and maintenance.
- A constant system monitoring to prevent equipment and network failures.
- An immediate reaction to an emergency to exclude business downtime.
Full IT Infrastructure Implementation
- An analysis of clients demands to determine required technology components.
- A detailed plan of works and expenses.
- An implementation with detailed regular reporting.
IT Audit and Consultancy
- An evaluation of an accuracy and efficiency of system operations.
- Understanding a company сapability to protect its information assets.
- An incidents roots determination to prevent potential disasters.
- A key technology risks specification.